By: Jesus Varela and James Flint
The Department of Defense has released an update to its Cloud Computing Security Requirements Guide (SRG) that fundamentally changes the landscape for cloud service providers seeking to serve high-security government workloads. The new CSP SRG v1r3, dated July 2, 2025, introduces changes that may have an impact on every cloud provider targeting Impact Level 5 authorizations.
Here’s what cloud service providers need to know immediately: Impact Level 5 Cloud Service Offerings now require implementation of National Security Systems (NSS) controls from CNSSI 1253. This translates to an additional 170 security controls, equating to a 40% increase from the previous requirements.
Background
The Cloud Computing (CC) Security Requirements Guide (SRG) was revamped in 2023 to:
- Include the changes instituted by NIST SP 800-53 Revision 5,
- Rely more on previously released FedRAMP and CNSS baselines and overlays, and
- Provide separation between the requirements that Mission Owners (MO) and Cloud Service Providers (CSP) must implement on all Cloud Service Offerings (CSO) employed by DoD components.
As of this writing, DoD has released three (3) versions of the new Cloud Computing SRG, identified by the year and month it was released:
- Cloud Computing SRG Y24M07 (released July 2024)
- Cloud Computing SRG Y25M01 (released January 2025)
- Cloud Computing SRG Y25M07 (released July 2025)
Contained within each of these SRG files, DoD has included:
- Cloud Computing Mission Owner Network SRG
- Cloud Computing Mission Owner Operating System SRG
- Cloud Service Provider SRG
- Clarifying documentation:
- Cloud Computing Mission Owner Overview
- Cloud Computing SRG Release Memo
- Cloud Computing SRG Revision History
- Readme SRG and STIG
The CSP SRG v1r1 was the initial release of the revamped SRG and included some significant changes to which FedRAMP baseline could support specific Impact Levels, how controls should be selected from supporting documentation, and identification of DoD specific selections and parameters for required controls. The table below describes how each SRG identifies baselines and the data that is allowed, by Impact Level.
FedRAMP+ Baselines and Allowed Data
| SRG | Impact Level 2 | Impact Level 4 | Impact Level 5 | Impact Level 6 |
| Cloud Computing SRG v1r4 [released 14 Jan 2022] | FedRAMP Moderate baseline Non-controlled Unclassified Information | FedRAMP Moderate or FedRAMP High baseline Controlled Unclassified Information (CUI) | FedRAMP Moderate or FedRAMP High baseline Controlled Unclassified Information and Unclassified National Security Information (U-NSI) | FedRAMP Moderate or FedRAMP High baseline Classified Information Up to SECRET (e.g., NSS) |
| Cloud Computing SRV Y24M07) [CSP SRG v1r1] [released 14 June 2024] | FedRAMP Moderate baseline Non-controlled Unclassified Information | FedRAMP Moderate or FedRAMP High baseline Controlled Unclassified Information (CUI) | FedRAMP High baseline Only Controlled Unclassified Information and Unclassified National Security System | FedRAMP High baseline Only Classified Information up to SECRET |
| Cloud Computing SRV Y25M01) [CSP SRG v1r2] [released 30 Jan 2025] | FedRAMP Moderate baseline Non-controlled Unclassified Information | FedRAMP Moderate baseline Controlled Unclassified Information (CUI) | FedRAMP High baseline Only Controlled Unclassified Information and Unclassified National Security System | FedRAMP High baseline Only Classified Information up to SECRET |
| Cloud Computing SRV Y25M07) [CSP SRG v1r3] [released 2 July 2025] | FedRAMP Moderate baseline Non-controlled Unclassified Information | FedRAMP Moderate or FedRAMP High baseline Controlled Unclassified Information (CUI) | FedRAMP High baseline Only Unclassified National Security System/National Security Information | FedRAMP High baseline Only Classified Information up to SECRET |
A major change with CSP SRG v1r1 was how DoD identified required controls for each Impact Level within the SRG itself. Specifically, as shown in the table above, CC SRG v1r4 allowed a CSP to utilize a FedRAMP Moderate or FedRAMP High authorized system for Impact Levels 4, 5, and 6. The CSP would then apply the SRG identified controls at the selected Impact Level as an overlay, and then be assessed. With CSP SRG v1r1, DoD provided significantly less SRG identified controls and relied on CNSSI 1253 for any additional controls.
In addition to the identified sources of controls in Table 3-1 of the CSP SRG, the CSP SRG identifies an additional 18-21 controls or enhancements (depending on Impact Level) that must be addressed by the Cloud Service Provider. Many of the controls have been previously selected by the FedRAMP Moderate or High baseline but have altered parameters identified by DoD. See Table D-1: FedRAMP+ Additions/Adjustments to Parameter Values for FedRAMP+ Security Controls/Enhancements of the CSP SRG for more details.
Cloud Service Provider (CSP) SRG v1r3
The newest version of the CSP SRG (v1r3) includes the following six high-level changes, some affecting other impact levels as well:
1. Updated guidance on Impact Level 4/5/6 categorizations and allowed data types
Impact Level 4 (IL4)
IL4 accommodates nonpublic, unclassified data (e.g., CUI and/or other mission data, including that used in direct support of military or contingency operations). See DoD CUI Program for more information. IL4 accommodates CUI information categorizations based on CNSSI-1253 up to moderate or high1 confidentiality and integrity (MMx or HHx2). CSPs can leverage either FedRAMP Moderate or FedRAMP High baselines in their journey of seeking an IL4 authorization.
No other changes to IL4 are identified in v1r3.
1CSP SRG v1r2 stated that IL4 accommodated information categorizations up to moderate confidentiality and integrity, whereas v1r3 states that IL4 accommodates information categorizations up to moderate OR high confidentiality and integrity.
2CSP SRG v1r2 stated that IL4 accommodated information categorizations up to MMx, whereas v1r3 states that IL4 accommodates information categorizations up to MMx AND HHx.
Impact Level 5 (IL5)
Impact Level 5 accommodates nonpublic, unclassified NSS/NSI3, including Controlled Unclassified Information requiring additional protection. The determination of whether CUI and/or mission data fits this category is up to the AO responsible for categorizing the information and choosing the Cloud Impact Level. IL5 accommodates NSS/NSI3 categorizations at CIA HHx.
3CSP SRG v1r2 stated that IL5 accommodated CUI and NSS, with information categorizations up to HHx, whereas CSP SRG v1r3 states IL5 accommodates NSS up to HHx, with a caveat that CUI can be hosted IF the AO determines a higher level of security is required, as deemed necessary by the information owner, public law, or government regulation.
Impact Level 6 (IL6)
IL6 accommodates non-public, classified NSS/NSI4 or non-public, unclassified data. Only information classified as SECRET or below, in accordance with the applicable executive orders, is permitted to be hosted at this Impact Level.
4CSP SRG v1r2 stated that IL6 accommodated NSS data, whereas v1r3 states that IL6 accommodates NSI (National Security Information) in addition to NSS data.
Additionally, a new note is included in v1r3 that states:
“Department of Defense Joint Warfighting Cloud Capability and Next Steps to Rationalize Cloud use Across the Department of Defense” memo dated 31 July 2023 should be reviewed as it states “all DOD Components, to include Military Departments (MILDEPs) and Combatant Commands (CCMDs), will leverage the JWCC contract vehicle for all available offerings for any new cloud computing capabilities and services at the Secret (Impact Level 6) or Top Secret, including all tactical edge and Outside the Continental United States (OCONUS) cloud computing capabilities and services.”
2. CSP SRG v1r3 Minimum DOD PA Assessment Controls
CSP SRG v1r3 provides Table 3-1 to identify the minimum controls that must be selected and responded to by the CSP.
Extract from CSP SRG v1r3 – Table 3-1: Minimum DOD PA Assessment Controls
| Impact Level | Baseline | Additional Controls Based on Data |
| 2 | FedRAMP Moderate | |
| 4 | FedRAMP Moderate or High, CNSSI 1253 Table D1 CIA MMx or HHx | Additional CNSSI 1253 Overlays |
| 5 NSS | FedRAMP High, CNSSI 1253 Table D1 “+”, CIA HHx | Additional CNSSI 1253 Overlays, CNSSI 1253 Table D1 “+” controls in CIA HHx |
| 6 NSS | FedRAMP High, CNSSI 1253 Table D1 “+” Classified Overlay, CIA HHx | Additional CNSSI 1253 Overlays, CNSSI 1253 Table D1 “+” controls in CIA HHx |
Utilizing the sources identified in Table 3-1, the following table identifies, at a high level, the minimum number of applicable controls per Impact Level. This does not account for any additional overlays that may be applicable to the system, such as the CNSSI Privacy Overlay.
Control Counts by Impact Level
| FedRAMP Mod + IL4 | FedRAMP High + IL4 | FedRAMP High + IL5 NSS | FedRAMP High + IL6 NSS |
| 344 | 428 | 600 | 628 |
The following table identifies, by source, the number of controls per Impact Level.
Control Source Breakdown by Impact Level
| Count of | FedRAMP Mod + IL4 | FedRAMP High + IL4 | FedRAMP High + IL5 NSS | FedRAMP High + IL6 NSS |
| FedRAMP Controls | 323 | 410 | 410 | 410 |
| DoD CSP SRG Controls | 21 | 18 | 20 | 19 |
| NSS (+) Controls CNSSI 1253 – H-H-x selections | — | — | 170 | 170 |
| Classified Overlay Controls CNSSI 1253E – Classified Overlay | — | — | — | 29 |
| Total | 344 | 428 | 600 | 628 |
*Note: Controls that are identified in multiple baselines/overlays are counted once.
3. New Section 5.1.4 Mission Owner (Customer) Responsibility Matrix/Configuration Guides
CSP SRG v1r3 now requires that CSPs provide their Mission Owners with a Customer Responsibility Matrix (CRM) similar to what FedRAMP requires for CIS/CRM. While CSPs who have started their authorization path through FedRAMP will already have this artifact available, any CSP that has not started down this road will now be required to provide this to all mission owners. Additionally, CSPs are also required to provide their Mission Owners configuration guides for all controls/control enhancements that the Mission Owner is responsible for, as identified in System and Services Acquisition (SA) control SA-5 System Documentation.
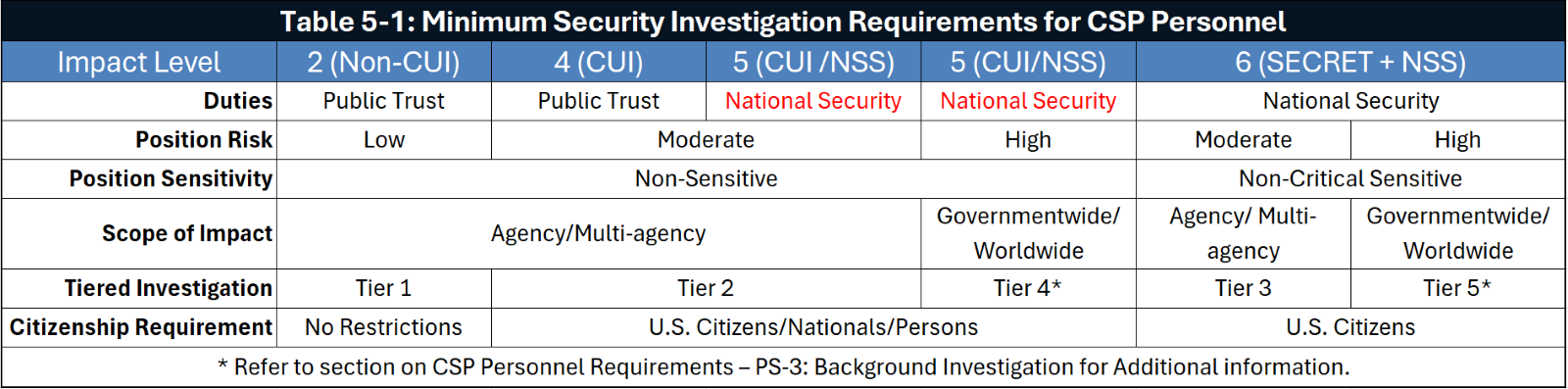
4. Update for CSP Personnel Background Investigation and Responsibilities
CSP SRG v1r3, section 5.5.2.2 CSP Personnel Requirements provides expanded information on the level of investigations required for CSP personnel, along with DoD’s justification for selecting each of the values shown below. Additionally:
- Investigation requirements may be elevated beyond the minimum as determined by the Mission Owner/AO.
- If CSP personnel require access to multiple cloud systems, they should undergo a background investigation commensurate with the highest level of access required.
As shown below in red text, Table 5-1 has been updated to indicate that the Duties of IL5 are now considered National Security, similar to IL6.
5. Update for Cyberspace Defense Actions
CSP SRG v1r3, section 6.1 Cyberspace Defense Actions, has been updated to include a new section on CSP Cyber Defense Activities. These actions must be completed prior to the onboarding of a Mission Owner and Cybersecurity Service Providers (CSSPs). Additionally, these activities may continue at the CSP level depending on the contract language or PA requirements. These activities include:
- Analyze cyber incidents and events.
- Monitor, protect, and defend CSP/CSO cloud-based systems, applications, and virtual networks, including privileged actions (e.g., cloud management or application administration) in the CSP’s/CSO’s infrastructure.
- Monitor for events or incidents against the Mission Owner applications (e.g., Structured Query Language [SQL] injection).
- Monitor, protect, and defend CSP cloud-based data in the CSO.
- Defend all connections to the CSO.
- Ensure internal communications are established between all entities performing Cyber Defense Activities.
- Provide visibility and awareness of cyber incidents or events impacting CSO systems, applications, virtual networks, and data as required in DOD PA.
6. Update for Cyberspace Defense and Incident Response
CSP SRG v1r3, section 6.2.2 Information Requirements, Categories, Timelines, and Formats, has been updated to require reporting of the ownership status of the facility hosting the physical system(s) of the CSO.
Final Thoughts
The DoD’s decision to implement NSS controls at IL5 represents both a challenge and an opportunity for the cloud service industry. While the additional 170 NSS controls may create a significant level of overhead, CSPs may already be implementing many of these controls or subsets of certain controls. This doesn’t mean that an increase in technical capabilities should be ignored, but CSPs should evaluate the capabilities they currently implement and perform a delta analysis against the 170 NSS controls. CSPs implementing the additional NSS controls at IL5 may find themselves in a position to cater to the DoD’s critical missions not considered classified.
Need help understanding how these new IL5 requirements affect your environment?
Contact us today for a targeted gap analysis and let our team help you assess the impact on your current implementation, prioritize remediation, and prepare for a successful DoD authorization path.






