Zero Trust Security? I’m pretty sure I’ve heard that before.
Perhaps the most straightforward definition of zero trust security is that it operates on the premise of implicitly trusting neither individuals nor devices. In the realm of cybersecurity, zero trust security represents an IT security paradigm demanding rigorous identity authentication for all users and devices seeking access to resources within a private network, irrespective of their location relative to the network perimeter.
A consistent element of Zero Trust Security is encapsulated within its seven foundational pillars, which delineate its architectural framework. While slight variations may exist across different sources, these seven pillars remain the most prevalent:
- Protecting the Workforce: The workforce security pillar ensures only authorized users access network resources by implementing authentication and access control policies, reducing the risk of unauthorized access and protecting sensitive data.
- Ensuring Device Integrity: Similar to workforce security, the primary objective of the device security pillar is to authenticate and authorize devices seeking to connect to enterprise resources. These devices could be under user control or fully autonomous, such as Internet of Things (IoT) devices. The pillar ensures that only trusted devices, regardless of their ownership or level of autonomy, are granted access to enterprise resources, thereby enhancing overall security posture and minimizing the risk of unauthorized access or malicious activities.
- Safeguarding Workload Security: The workload security pillar encompasses the protection of applications, digital processes, and both public and private IT resources utilized by an organization for operational purposes. Security measures are implemented around each workload to thwart unauthorized access, tampering, or data breaches, thereby safeguarding sensitive applications and services.
- Securing Network Pathways: The network security aspect of the zero-trust framework serves to meticulously segment and isolate critical resources, preventing unauthorized individuals or entities from gaining access to them.
- Implementing Zero-Trust Data Protection: This pillar of zero-trust emphasizes categorizing corporate data, isolating it to authorized personnel only, and determining its storage location, alongside employing encryption for data both in transit and at rest.
- Improving Visibility and Harnessing Analytics: All security procedures related to access control, segmentation, encryption, and the organization of applications or data require meticulous monitoring. The visibility and analytics aspect may advocate for employing AI to automate certain processes, such as anomaly detection, configuration management, and achieving comprehensive end-to-end data visibility.
- Optimizing Automation and Orchestration Processes: The last cornerstone of the zero-trust framework addresses contemporary methods through which organizations can automate and centrally manage the entire zero-trust model across LAN, WAN, wireless WAN, and public or private data centers.
In addition to the seven pillars, the Cybersecurity & Infrastructure Security Agency (CISA) and the National institutes of Standards and Technology (NIST) recommend including the following cross-cutting capabilities to further mature and enforce Zero Trust Security within your company or agency:
- Visibility and Analytics: Gain comprehensive insights into network activity, user behavior, and potential security threats, enabling proactive risk management and decision making.
- Automation and Orchestration: Streamline security operations, facilitate rapid response to threats and enforce consistent policy enforcement across various environments and devices.
- Governance: Implement a Zero Trust Security model to ensure adherence to security policies, compliance regulations, and best practices throughout the organization or agency’s infrastructure and operations.
Linked to the pillars listed above are the four different maturity stages. According to CISA, “each subsequent stage requires greater levels of protection, detail, and complexity for adoption.” Below are the criteria for identifying maturity in each of the pillars.
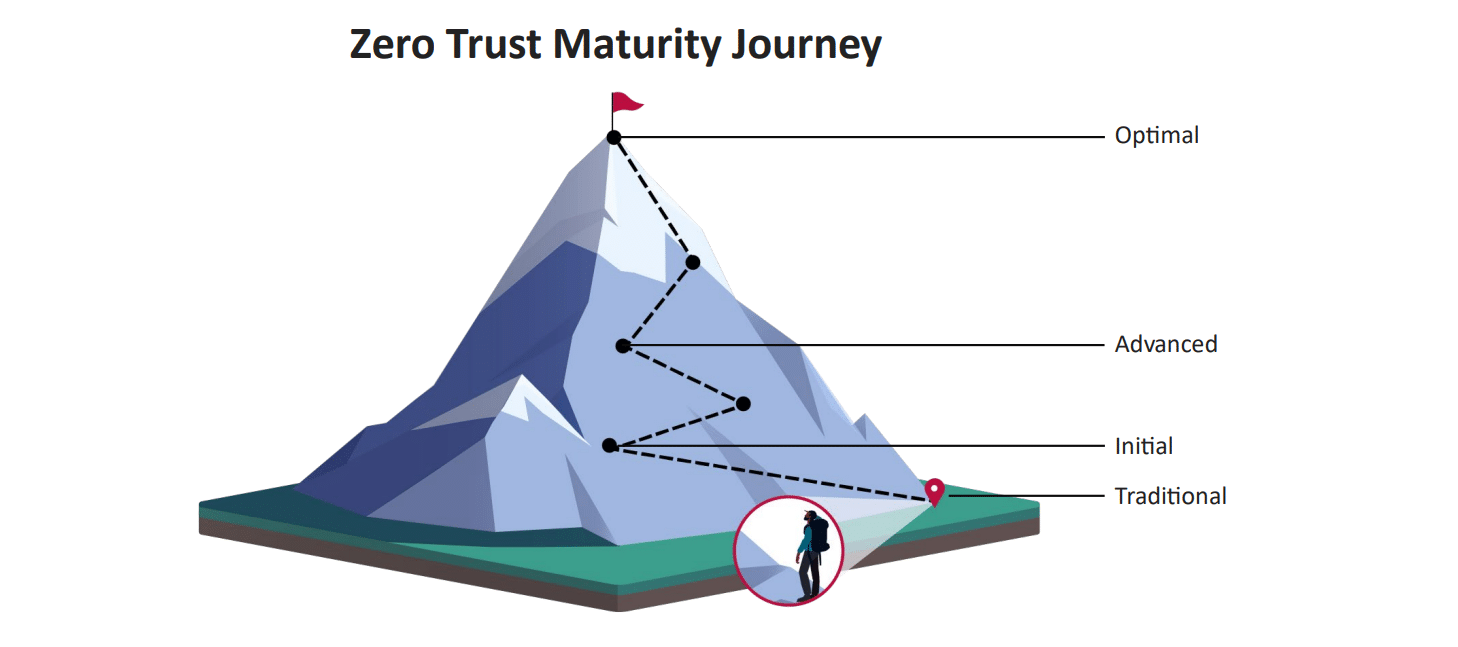
- Traditional: Integration of Zero Trust Security principles into established infrastructure and practices to enhance security and mitigate risks associated with traditional network architectures.
- Initial:
- Begin using automation of assigning certain attributes and configuring policies
- Initial phase of kicking off the cross-pillar integration of external systems
- Advanced:
- Automated controls that are for the lifecycle of configurations and policies that reach across all pillars
- Establishes centralized visibility and control over identities, with policy enforcement
- Enabling predefined mitigations in response to identify risks, adjusting least privilege based on security risk posture and ongoing assessments.
- Optimal:
- Fully automated, leverages resources like self-reporting with dynamic policies based on monitored and automated triggers.
- Dynamic least privilege access
- Continuous validation
And finally, here are two additional points to keep in mind when considering Zero Trust:
- Secure Supply Chain: Broaden the application of Zero Trust Security Principles to encompass third-party vendors, partners, and suppliers, thereby safeguarding the security of the entire supply chain.
- Incident Response and Remediation: Establish resilient incident response capabilities to promptly identify, contain, and address security incidents within the Zero Trust Security framework.
Looking to implement zero trust in your organization? 38North Security can help. Get in touch with a security professional today.




