Developed in partnership between FedRAMP and NIST, OSCAL (aka Open Security Controls Assessment Language) is an security compliance automation initiative. The program is designed to expedite the implementation of security deliverables associated with government authorization packages. It’s an initiative to help streamline and automate the publication, implementation, and assessment of security controls.
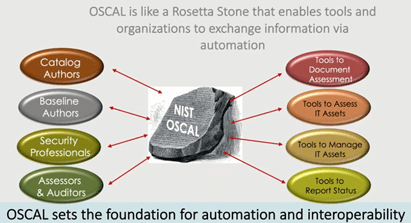
OSCAL In Real World Use
Although in its infancy, the program has already been adopted by a handful of organizations and, according to an OSCAL workshop presentation, shown promising results.
Given the right amount of upfront investment, organizations can build around the OSCAL framework to automate the continuous monitoring and implementation of NIST security controls and FedRAMP baselines. While adoption has been slow, several notable organizations currently integrate OSCAL into product and service offerings.

What OSCAL Looks Like
Looking at the two pictures below, the one on the left is how the AC-1 NIST 800-53 control is depicted in JSON. OSCAL data will also be available in YAML and XML. NIST plans on making the entire 800-53 rev5 catalog available in all three OSCAL formats.
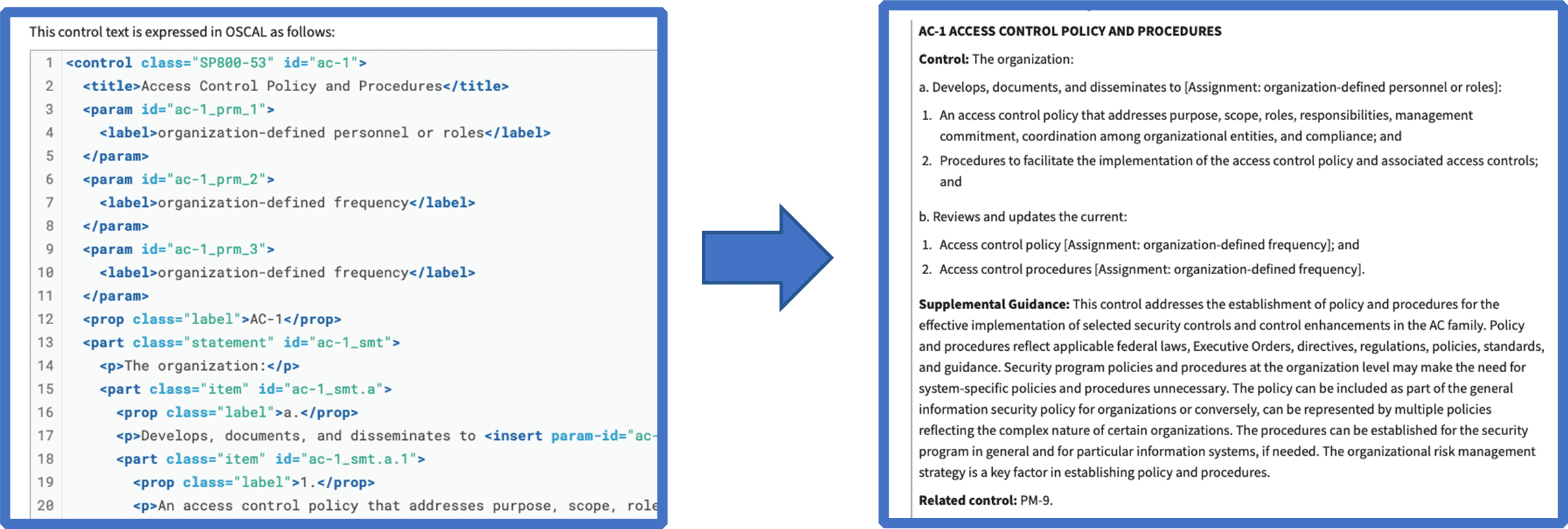
The picture on the right of the AC-1 control documentation is produced by the demonstration tool. The controls can all feed other layers of OSCAL; such as FedRAMP baselines and System Security Plans (SSPs). NIST has prepared a simple demonstration tool that NIST tool that processes raw OSCAL data into a finished product, without any human intervention.
Expected OSCAL Benefits
By applying OSCAL to the NIST control catalogue, FedRAMP baselines, and security deliverables, the OSCAL program hopes to provide the following benefits to their respective stakeholders:
| Role | Benefits |
| Executives | Simplify and expedite cloud solutions certification and authorization. Analyze and decide compliance needs using data from all sources, reducing the need for technical expertise. Improving an organization’s overall security by re-allocating resources to security operations. |
| Compliance Program Managers | Provide them a solution to ingest requirements into tools to map and reconcile any/all frameworks. Create and manage all artifacts generated by your systems. Enable the automation of developing, reviewing and maintaining FedRAMP security deliverables such as SSPs and IDRs. |
| System Operations Managers | Monitor and assess implementations using data from all sources. |
| Assessors | Focus on evaluating controls and requirements that need real expertise and dramatically reduce the time spent evaluating screenshots. Include validation rules to enable automated package reviews. |
| Controls and Framework Authors | Update knowledge to keep up with threat environment. Quickly and efficiently push out the latest set of outcomes, controls, and countermeasures. |
OSCAL Limitations
While our first look at OSCAL was full of excitement at its potential to automate meticulous and repetitive cybersecurity compliance tasks, it also revealed some limitations. NIST is still waiting for the industry to develop the tools needed for organizations of all sizes to fully harness its power, judging from NIST’s official workshop presentations. But as of now, organizations interested in using OSCAL will need to develop their own OSCAL-compatible tools. Additionally, everyone involved in the compliance process will need to be trained on how to utilize OSCAL and optimize their time and effort.
The Future of OSCAL
OSCAL is a much-needed framework to help organizations automate tasks along the cybersecurity compliance process. As the industry adopts OSCAL, more and more tools and resource will be available to help integrate OSCAL into the compliance and authorization processes. However, for organizations able to put the upfront investment, OSCAL is already a promising prospect.
Contact 38North to learn more about how you can use OSCAL to help automate security compliance.




