Cloud technology is revolutionizing how government agencies operate, but with great power comes great responsibility – especially when it comes to security. Enter StateRAMP and FedRAMP, two certification programs that make sure cloud providers aren’t playing fast and loose with sensitive government data. While these programs might sound similar (and let’s face it, government loves its acronyms), they’re actually quite different.
We’re going to break down what differentiates StateRAMP and FedRAMP from each other. We’ll look at where they came from, who they’re for, and how they work. Whether you’re a government agency trying to figure out which standard to follow, or a cloud provider looking to expand your government clientele, understanding these differences is key to navigating the sometimes (often?)-murky waters of public sector cloud security.
What is FedRAMP?
The more widely known Federal Risk and Authorization Management Program or FedRAMP emerged in 2011 as a response to the rapidly increasing adoption of cloud services by federal agencies. Recognizing the need for standardized security measures, the U.S. government established a set of comprehensive guidelines. By 2012, FedRAMP was fully operational, with the General Services Administration (GSA) overseeing its implementation and management across federal agencies.
Learn more: FedRAMP Certification Requirements: 27 Documents and Processes to Get Familiar With
What is StateRAMP?
The State Risk and Authorization Management Program or StateRAMP made its debut in 2020. FedRAMP was well-established at the federal level, leaving state and local governments lacking a similar standardized approach to cloud security.
Recognizing this gap, a coalition of state government leaders, industry experts, and former FedRAMP officials came together to create a solution. Their collaborative effort resulted in the formation of StateRAMP, a program tailored to address the specific cloud security needs of state and local governments.
StateRAMP incorporates key elements of FedRAMP, modified to suit the unique requirements of state and local governments, and aims to guide these entities through the complex landscape of cloud security.
While both programs share the core mission of safeguarding government data in cloud environments, they operate in distinct spheres. FedRAMP focuses on national-level implementation, whereas StateRAMP serves as a more localized solution for state and municipal governments.
Why choose StateRAMP?
FedRAMP is known for its rigorous standards, often described as the gold standard in government cloud security. The process typically spans 12 to 18 months and can cost upwards of a million dollars. Adding to the challenge, cloud service providers (CSPs) must secure a federal agency sponsor to navigate the authorization process. These factors make FedRAMP a significant undertaking, especially for smaller or mid-sized companies.
Learn more: Understanding FedRAMP Certification Cost: A Breakdown of Expenses and Tips to Reduce Them
StateRAMP, by contrast, offers a more accessible path to security verification for state and local government cloud services. While still maintaining high standards, StateRAMP generally requires less time and financial investment than its federal counterpart. Notably, it doesn’t require a government sponsor to initiate the process, lowering the barrier to entry for many CSPs.
For many companies, achieving StateRAMP authorization can serve as a valuable intermediate step towards eventual FedRAMP authorization.
Authorization Processes: FedRAMP vs. StateRAMP
Let’s take a look at the authorization processes companies go through in order to become FedRAMP authorized and StateRAMP authorized.
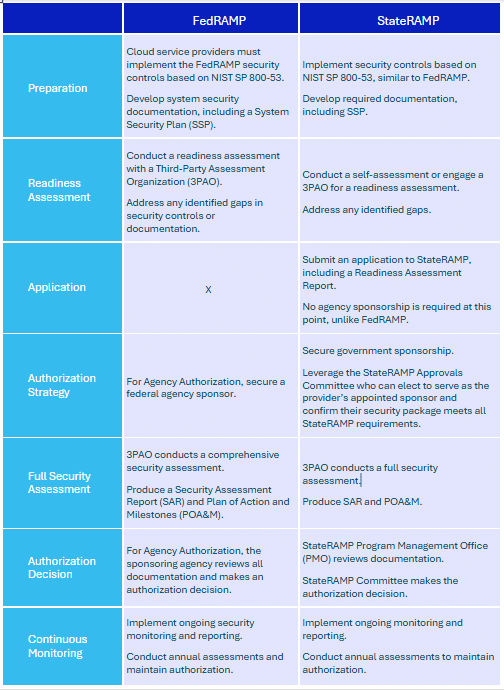
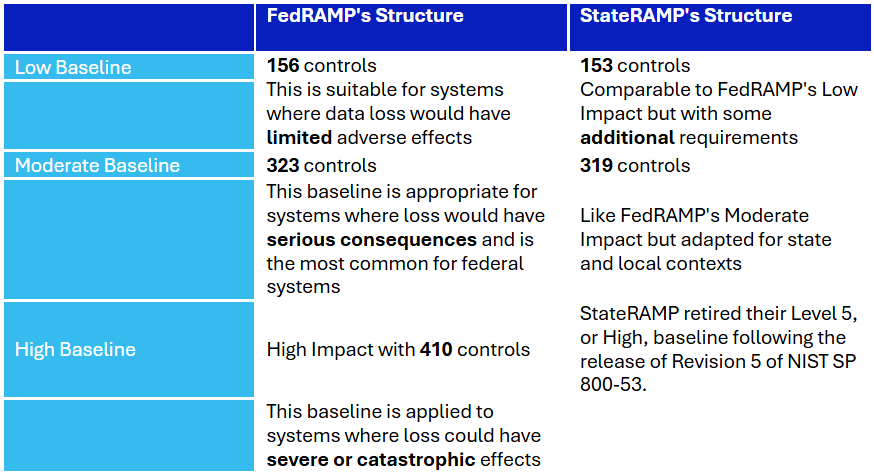
Security Baselines: FedRAMP vs. StateRAMP
NIST SP 800-53 Foundation:
Both FedRAMP and StateRAMP use NIST SP 800-53 as their foundation, and both employ tiered security baselines, tailored to the potential impact of data loss on organizational operations.
StateRAMP offers different levels of authorization (Low and Moderate Impact Levels) to accommodate varying security needs and provider capabilities. This tiered approach allows cloud service providers to start at a level appropriate to their current security posture and gradually work towards higher levels of authorization.
How are they implemented?
The implementation approach is similar for both: cloud service providers must identify the appropriate baseline, implement required controls, document the implementation in their System Security Plan, undergo assessment by a Third-Party Assessment Organization, and continuously monitor and maintain their security posture post-authorization.
Ultimately, the choice between FedRAMP and StateRAMP baselines often depends on the target market of the cloud service provider and the specific requirements of their potential government clients, with many finding StateRAMP certification a valuable step towards eventual FedRAMP authorization.
Reciprocity Between FedRAMP and StateRAMP
FedRAMP authorization is generally accepted by StateRAMP, but not vice versa. However, StateRAMP can be a steppingstone towards FedRAMP.
The choice between pursuing FedRAMP or StateRAMP authorization often depends on a cloud service provider’s target market, resources, and long-term goals in the government sector.
Key Differences:
- Sponsorship: FedRAMP requires a federal agency sponsor to begin the process of Agency Authorization, while StateRAMP does not require sponsorship until after the 3PAO assessment.
- Governing Body: FedRAMP is overseen by the FedRAMP PMO, while StateRAMP is managed by its own PMO and committee.
- Scope: FedRAMP focuses on federal government use, while StateRAMP is tailored for state and local governments.
- Flexibility: StateRAMP allows for more flexibility in accommodating state-specific requirements.
- Complexity and Cost: While both are rigorous, StateRAMP is generally less complex and costly than FedRAMP.
- Timeline: StateRAMP authorization typically takes less time to achieve than FedRAMP.
While FedRAMP remains the gold standard for federal cloud service security, StateRAMP provides a valuable alternative for cloud service providers looking to demonstrate their security capabilities and access local government markets.
More questions? Want to chat?
Navigating the complexities of StateRAMP can be a challenge, but you don’t have to go it alone. At 38North Security, we have a team of experienced, friendly StateRAMP experts who are passionate about helping organizations like yours understand and comply with these important regulations.
Our consultants are excellent communicators who are dedicated to breaking down the complexities of StateRAMP in easy-to-understand terms. Whether you prefer in-depth discussions or quick Q&A sessions, we are here to address all your questions and concerns, ensuring you feel confident and informed throughout your StateRAMP journey.
We are eager to learn about your unique needs and will work closely with you to develop a tailored strategy for success. We’ll also help you select from third party assessment organizations to find the best one to partner with.
Learn more: CSPs: Here’s How to Choose the Right FedRAMP 3PAO to Partner With
So, if you’re ready to get started with StateRAMP or if you simply have some lingering questions, we encourage you to reach out to our team. We’re excited to share our knowledge, provide personalized guidance, and help you navigate the path to successful StateRAMP authorization.





