Table Of Contents
-
Key Takeaways
-
Understanding CMMC Levels: A Brief Overview
-
How the DoD Determines Required CMMC Levels
-
Identifying Your Organization's Data Type
-
Steps to Achieve Your Required CMMC Level
-
The Role of CMMC Third-Party Assessment Organizations (C3PAOs)
-
Cost Implications of Achieving CMMC Compliance
-
Benefits of Achieving CMMC Compliance
-
Preparing for Your CMMC Assessment
-
Summary
-
Frequently Asked Questions
Determining ‘what CMMC level do I need’ hinges on the kind of data your company processes for Department of Defense (DoD) contracts. This concise guide helps you swiftly pinpoint whether Level 1, 2, or 3 of the Cybersecurity Maturity Model Certification (CMMC) is right for you by simplifying the decision-making factors into understandable terms. Avoid the guesswork and secure your business’s defense contract eligibility with the correct level of CMMC compliance.
Key Takeaways
- The CMMC model has three certification levels, requiring adherence to a progressively advanced set of cybersecurity practices, with Level 1 focused on Federal Contract Information (FCI) and Level 2 and Level 3 dealing with Controlled Unclassified Information (CUI) and more advanced practices.
- DoD contractors must determine the appropriate CMMC level based on the data type handled, with required levels specified in DoD solicitations and RFIs, and must go through a comprehensive process involving gap analysis, implementing controls, staff training, and potentially engaging consultants.
- Attaining CMMC compliance involves costs that vary by organizational size and complexity, with benefits including a competitive edge in securing DoD contracts and an enhanced cybersecurity posture; preparation for the assessment is crucial, including organizing evidence for review.
Need help fulfilling CMMC requirements? Get started — speak to a cybersecurity expert today.
Understanding CMMC Levels: A Brief Overview
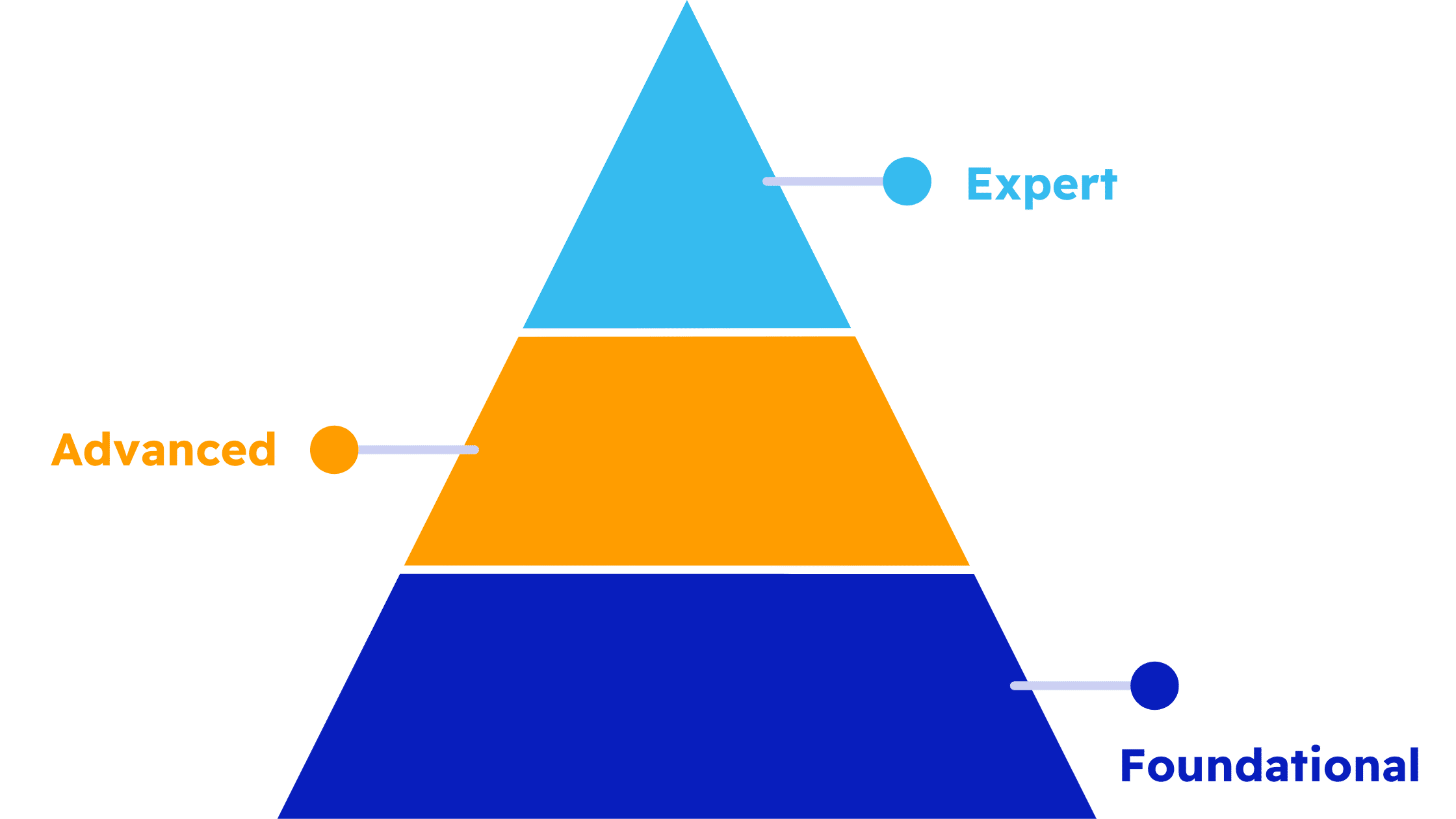
The CMMC is a certification program established by the DoD. Its purpose is to enhance supply chain security within the defense industrial base (DIB). The ultimate aim is for all contractors to be certified to one of the three CMMC levels. This certification is important for ensuring compliance and security standards. Each of these levels focuses on protecting different types of information, requiring adherence to a specific set of cybersecurity practices.
Understanding these levels and their corresponding requirements is critical for any organization aiming to achieve CMMC compliance. To get a detailed understanding of each control and the differences between CMMC maturity levels, it’s recommended to read the CMMC Assessment Guides and Appendices.
Learn more: What is CMMC Compliance? A Brief Intro for CSPs Exploring Certification
Level 1: Foundational Cyber Hygiene
Starting at the base, CMMC Level 1 certification primarily focuses on the protection of Federal Contract Information (FCI). Organizations at this level are required to implement 17 basic cybersecurity practices to secure FCI. These practices can be performed in an ad-hoc manner without the need for formal documentation.
FCI is a specific type of information that is not intended for public release. It is provided by or generated for the Government under a contract to develop or deliver a product or service. The basic safeguarding requirements for this type of information are outlined in 48 CFR 52.204-21.
Level 2: Advanced Cyber Hygiene
At Level 2, the CMMC takes a step up, with the focus shifting towards the protection of Controlled Unclassified Information (CUI). Organizations aiming for this level must demonstrate advanced cyber hygiene by implementing all 14 domains and 110 security controls of NIST 800-171 rev2. (Note that although revision 3 of NIST SP 800-171 has been published, the CMMC program continues to operate on revision 2 until further notice.)
The requirements for Level 2 are detailed in the CMMC 2.0 Model and Assessment Guide, which provides comprehensive information on the requisite practices and processes. From monitoring user activities to implementing data recovery processes, a broad spectrum of cybersecurity practices come into play.
However, it’s not just about implementing these controls. For Level 2 certification, organizations must also document their processes, supporting the implementation of advanced cybersecurity practices specific to this level. This documentation is critical in demonstrating compliance to CMMC assessors.
Level 3: Expert Cybersecurity
At the apex of the CMMC pyramid lies Level 3, with its focus on expert cybersecurity practices. To achieve this certification, organizations must demonstrate compliance with all 130 security controls in NIST SP 800-171 rev2, along with other practices based on NIST SP 800-172.
This level is intended for organizations that handle highly sensitive CUI, particularly for DoD programs classified as a high priority. It is estimated that only a tiny fraction of contractors engaged with advanced war-fighter solutions will require CMMC Level 3 certification.
Learn more: CMMC vs. FedRAMP: What’s the Difference?
How the DoD Determines Required CMMC Levels
The DoD determines the required Cybersecurity Maturity Model Certification (CMMC) levels for defense contractors based on several key factors related to the sensitivity and criticality of the information being handled. Here’s a detailed overview of the process:
- Type of Information Handled:
- Federal Contract Information (FCI): This is information provided by or generated for the government under contract that is not intended for public release. Contractors handling FCI typically need to meet CMMC Level 1, which focuses on basic safeguarding requirements.
- Controlled Unclassified Information (CUI): This is information that requires safeguarding or dissemination controls pursuant to federal law, regulations, and government-wide policies. Contractors handling CUI typically need to meet at least CMMC Level 2, which includes more comprehensive security practices.
- Risk Assessment:
- The DoD assesses the potential risks associated with the loss, compromise, or unauthorized access to the information being handled. This includes considering the impact on national security, operational capabilities, and mission success.
- Criticality of the Contractor’s Role:
- The DoD evaluates the importance of the contractor’s role in the supply chain. Contractors involved in critical programs, systems, or technologies may be required to CMMC Level 3 to ensure robust protection against advanced persistent threats (APTs).
- Contract Requirements:
- Specific contract requirements may dictate the necessary CMMC level. The DoD incorporates CMMC requirements into the contract language, specifying the level required for the contractor and any subcontractors.
- Nature of the Work:
- The nature and scope of the work performed by the contractor can influence the required CMMC level. For example, contractors involved in research and development (R&D), production, or maintenance of sensitive defense systems may require higher levels of certification.
Identifying Your Organization’s Data Type
A fundamental step in determining your required CMMC level is identifying the type of data your organization handles. This could range from public information, which does not require CMMC certification, to Federal Contract Information (FCI) and Controlled Unclassified Information (CUI).
DoD contractors and subcontractors handling CUI need to meet CMMC Level 2 certification requirements, at a minimum. Therefore, by correctly identifying your data type, you can map your path towards the appropriate CMMC level.
Steps to Achieve Your Required CMMC Level

Achieving CMMC compliance is not a single-step process; it involves a series of steps, from conducting a gap analysis to training staff and engaging consultants.
Every organization’s path to CMMC certification will be unique, influenced by its existing cybersecurity practices, internal resources, and the level of CMMC compliance it seeks to achieve.
Gap Analysis
A gap analysis is a crucial first step in the path to achieving CMMC compliance. It involves an internal cybersecurity assessment used to understand the improvements needed to meet CMMC standards. For Levels 2 and 3, this assessment leverages NIST SP 800-171A and 800-172A guidelines to assess an organization’s current controls across various aspects, identifying areas where cybersecurity enhancements are needed.
But it doesn’t stop at identifying the gaps. Post gap analysis, it’s essential to develop an improvement plan, which includes identifying training requirements to ensure staff can competently demonstrate the controls during a CMMC assessment.
Implementing Controls
Once the gaps have been identified, the next step is to implement the necessary controls. Achieving CMMC compliance requires a consistent approach that integrates:
- Policy
- Training
- Process
- Resilience considerations
Implementing these measures often results in infrastructure and technology enhancements, as part of the remediation process. Depending on the resources available, organizations can undertake this implementation through various methods, such as in-house, with assistance from consultants, or via done-for-you solutions from managed security service providers, all while ensuring the security of publicly accessible system components and utilizing a supplier performance risk system.
Staff Training
Staff training is a pivotal part of achieving CMMC compliance. After all, the best cybersecurity practices are only as good as the people who implement and manage them. Training encompasses educating managers, systems administrators, and users on the security risks connected with their activities and the related policies, standards, and procedures.
Moreover, the training programs must also include guidance on detecting and handling potential indicators of insider threats, as well as advanced persistent threats, to maintain robust national security protocols for authorized users and implement malicious code protection mechanisms.
Security awareness can be enhanced through visual aids like posters, serving as constant reminders of security best practices and reinforcing the importance of a system security plan.
Engaging Consultants (RPOs)
Navigating the complex landscape of CMMC compliance can be daunting, and that’s where consultants come in. Registered Practitioner Organizations (RPOs) employ individuals that have been trained specifically on CMMC requirements. Engaging RPOs can provide essential expertise, guiding organizations through the complex assessment process.
RPOs can offer the following benefits:
- Access to certified and experienced cybersecurity professionals trained in the CMMC ecosystem
- More accurate and efficient guidance, ultimately saving time and financial resources
- Improved understanding and oversight of an organization’s cybersecurity practices
The Role of CMMC Third-Party Assessment Organizations (C3PAOs)
Now, let’s talk about CMMC third-party assessment organizations, also known as C3PAOs. These organizations play a crucial role in the CMMC compliance process, being responsible for evaluating an organization’s cybersecurity practices. But becoming a C3PAO is no small feat. They must:
- Successfully pass a CMMC maturity level 3 assessment
- Meet legal ownership requirements
- Obtain certifications such as ISO 17020 within a specified timeframe.
Once authorized by the CMMC accreditation body, C3PAOs undertake a comprehensive evaluation process, including reviewing security documentation, conducting interviews, and performing on-site inspections. Following this evaluation, they issue certificates of adherence to CMMC standards, validate compliance, and may recommend corrective actions if gaps are identified.
Cost Implications of Achieving CMMC Compliance
While achieving CMMC compliance is a necessity for DoD contractors, it does come with its own set of costs. These costs are influenced by factors such as:
- Organizational size
- Complexity
- Type of cybersecurity protocols used
- CMMC level required
It’s important to note that achieving CMMC compliance requires an ongoing investment in time and financial resources even post-certification to maintain compliance. However, organizations can reduce compliance costs by:
- Narrowing the compliance boundary
- Optimizing the use of compliance documentation packages
- Engaging certified consultants
- Aligning certification efforts with the budget.
Benefits of Achieving CMMC Compliance
Despite the costs and challenges, achieving CMMC compliance carries several benefits. One of the most direct benefits is competitive advantage. Early CMMC certification could significantly reduce competition for DoD contracts, giving compliant businesses advantages in securing these lucrative opportunities.
Beyond the competitive advantage, achieving CMMC compliance enhances an organization’s cybersecurity posture by mandating implementation of best practices that mitigate risks and protect against cyber breaches. It also allows a tailored approach to cyber hygiene, aligning cybersecurity efforts with the specific threats and sensitivity of data an organization handles.
Preparing for Your CMMC Assessment
As you inch closer to your CMMC assessment, preparation is key. Contractors who have already implemented all controls in NIST SP 800-171 should find that they are well-prepared for a CMMC 2.0 assessment up to Level 2.
When the time comes for the actual CMMC assessment, schedule a time with a C3PAO and have all necessary evidence organized and accessible for the assessment team to review. This proper organization and preparedness can go a long way in ensuring a smooth and successful assessment process.
Learn more: What to Expect When You’re Expecting a FedRAMP 3PAO Assessment
Summary
Throughout this guide, we’ve navigated the intricate landscape of CMMC compliance, exploring its levels, identifying data types, understanding the role of DoD, RPOs and C3PAOs, and outlining the steps to achieving compliance. Beyond the complexities and costs, it’s clear that achieving CMMC compliance is a strategic necessity for DoD contractors. It’s an investment in strengthening cybersecurity practices, protecting sensitive information, and securing a competitive advantage in the lucrative DoD contracting landscape.
38North Security can help you decipher which CMMMC level your cloud offering needs — and find the best path to achieving certification. Speak to one of our cybersecurity experts today.
Frequently Asked Questions
What CMMC 2.0 level do I need?
You will need CMMC Level 2 compliance if your business processes, handles, or manages information critical to national security for the Department of Defense in the form of FCI or CUI.
Who needs CMMC 2.0 Level 3?
CMMC 2.0 Level 3 applies to companies that handle CUI for DoD programs with the highest sensitivity.
Who needs CMMC Level 1?
DoD contractors and subcontractors that handle FCI provided by, or generated for, the government under a contract to develop or deliver a product or service to the government need CMMC Level 1 to perform basic cybersecurity practices.
What are the 5 CMMC levels?
The latest CMMC 2.0 model only has three levels: Level 1 (Foundational), Level 2 (Advanced), and Level 3 (Expert). These levels replaced the original five-tier system in CMMC 1.02.
What is the CMMC?
The CMMC, also known as the Cybersecurity Maturity Model Certification, is a program by the Department of Defense (DoD) to enforce cybersecurity best practices among defense contractors.
Table Of Contents
-
Key Takeaways
-
Understanding CMMC Levels: A Brief Overview
-
How the DoD Determines Required CMMC Levels
-
Identifying Your Organization's Data Type
-
Steps to Achieve Your Required CMMC Level
-
The Role of CMMC Third-Party Assessment Organizations (C3PAOs)
-
Cost Implications of Achieving CMMC Compliance
-
Benefits of Achieving CMMC Compliance
-
Preparing for Your CMMC Assessment
-
Summary
-
Frequently Asked Questions





