Vulnerabilities are inevitable in information systems. New vulnerabilities are discovered daily – and if you’re not careful, they can spiral out of control pretty fast.
That’s why vulnerability management should be assigned to personnel with dedicated roles and responsibilities for remediating them. A key component of this task and the overall security of the system for FedRAMP or CMMC compliance is documenting and tracking POA&Ms.
What is a Plan of Action and Milestones (POA&M)?
A POA&M is simply a way to track open vulnerabilities within the information system. FedRAMP describes it as, “a key document in the security authorization package and monthly continuous monitoring activities. It identifies the system’s known weaknesses and security deficiencies, and describes the specific activities the CSP will take to correct them.”
POA&Ms can be documented in a variety of ways to track the vulnerabilities and closure timeframes. You can, for example, use a spreadsheet or even a third-party application. The Federal Risk and Authorization Management (FedRAMP) Program makes it easy by providing a template that can be used across other security frameworks, such as CMMC, etc. FedRAMP also provides guidance on how to complete the POA&M by providing a template completion guide. Some key items to include are the system, vulnerability, vulnerability ID, date discovered, and expected remediation date. Additional items that could also be added are the corresponding service tickets that track what personnel are responsible for remediation.
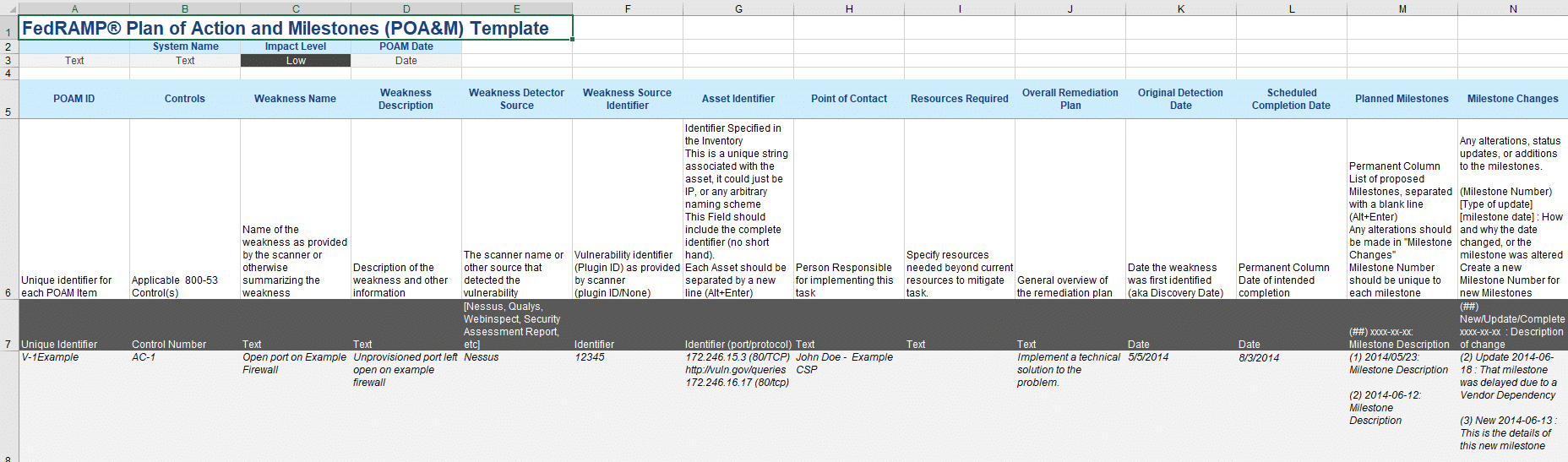
Why Both FedRAMP and CMMC Require a POA&M
FedRAMP and CMMC both require organizations to develop a POA&M as part of their compliance process for different reasons:
- Risk Management: POA&M is a fundamental tool for managing risks. It allows organizations to identify vulnerabilities, weaknesses, and deficiencies in their systems and processes. By listing these issues along with planned actions and milestones for remediation, organizations can effectively manage and prioritize their efforts to mitigate risks. In other words, having a list of vulnerabilities in one place, and their corresponding actions, keeps everyone organized.
- Compliance: Both FedRAMP and CMMC have stringent compliance requirements related to cybersecurity. A POA&M demonstrates that the organization is actively working to address any identified weaknesses or deficiencies in its systems and processes. It serves as evidence of the organization’s commitment to achieving and maintaining compliance.
- Transparency and Accountability: A POA&M provides transparency into an organization’s cybersecurity posture by documenting known weaknesses and the steps being taken to address them. This transparency is essential for building trust with stakeholders, including government agencies, customers, and partners. It also holds the organization accountable for addressing identified vulnerabilities within a reasonable timeframe.
- Continuous Improvement: Cyber threats and vulnerabilities evolve rapidly. POA&M facilitates a continuous improvement approach to cybersecurity by encouraging organizations to regularly assess their systems and processes, identify new risks, and implement measures to mitigate those risks. This iterative process helps organizations stay ahead of emerging threats and enhance their overall cybersecurity posture over time.
Similar to the principle of a software bill of materials, a POA&M provides visibility into vulnerability management, documentation, and a foundation for building a stronger cybersecurity posture.
Learn more: Three Ways a Software Bill of Materials Beefs Up Supply Chain Security
Developing, Implementing, & Maintaining POA&Ms: Rules vs. Reality
For organizations adhering to FedRAMP, the Risk Assessment (RA) control family in the FedRAMP control baseline provides the vulnerability closure timeframes that must be adhered to when drawing up POA&Ms. Specifically, Critical and High findings must be closed within 30 days, Mediums in 90 and Lows within 180 days, with the countdown starting on the date of discovery. For systems in Continuous Monitoring (ConMon), these findings are reported monthly.
That said, modern systems, especially cloud-based ones, often scan continuously. So does the countdown really start the second a finding shows up on a scan?
In actual practice, the answer is no. Here’s what most organizations do: At the beginning of each month, right after the ConMon report is submitted, an organization performs informational scans to see what vulnerabilities exist in the system. They then close what they can before running a formal ConMon scan that serves as the basis for reporting.
This is a gray area within FedRAMP, but by scanning your system at the beginning of the month you essentially “buy time” to get the vulnerabilities remediated before running official scans at the end of the month and completing the POA&M, which is submitted to the PMO or the JAB. By doing scans at the beginning of the month it allows the CSP to work on high and moderate findings before the remediation timelines begin which is discussed below. Once a vulnerability is remediated, it should be moved to a closed tab or clearly delineated that it is closed.
For FedRAMP specifically, during the annual assessment, a 3PAO will want to validate POA&Ms are performed by observing at least three iterations of the most recent POA&Ms. Typically, CSPs maintain a SharePoint or similar site for each month’s POA&Ms and keep them indefinitely or for at least a year. It is important to note that all POA&Ms, as well as any corresponding tickets, should be stored within the boundary because of the metadata (IPs, & Hostnames) within each POA&M item.
Is It Ever Okay to Keep Vulnerabilities Open Past Remediation Timeframes?
As noted above, POA&M items must be remediated within the FedRAMP Low, Moderate, and High vulnerability timeframes, which are 30, 90, and 180 days, respectively. If vulnerabilities cannot be remediated during those timeframes, then an explanation within the POA&M item needs to be documented along with supporting evidence. Vendor dependencies can also remain on the POA&M past the remediation timeframes. A vendor dependency is when a vulnerability cannot be remediated because the system component or operating system on the component is only able to be patched but a firmware or image update.
For example, when I worked for a Cloud Service Provider, I was responsible for the remediation of vulnerabilities for the WIDS (Wireless Intrusion Detection System). One vulnerability could not be remediated, as it was a false positive because of the Linux overlay for the appliance; but it was showing up as a vulnerability in weekly scans for that system.
In an email exchange with the vendor, they explained that limitations existed with the engineering team preventing it from being remediated immediately. The next quarterly release for the WIDS appliance would fix the vulnerability so that consequently it would no longer show up in vulnerability scans. Because of the Linux overlay, it was not an urgent issue as a defense in depth was acting as a compensating control, as accessing the OS was restricted. The WIDS was an application on an appliance on the Linux system.
During the assessment, I provided the auditor, who assessed the WIDS I managed, the justification on why the vulnerability was still open. I included the email chain that demonstrated the work with the vendor to resolve the vulnerability. Each month, I updated the POA&M to provide an update on when the engineering team was going to remediate the issue. I provided an updated time frame within that POA&M item linking the artifacts for the open item until the item was remediated. Deviation requests or operation requirements can be submitted to the agency, but you cannot accept your own risk.
CMMC’s Stance
Here’s the breakdown on what’s permitted for CMMC:
CMMC Level 1: No POA&Ms are permitted.
CMMC Level 2:
- Assessment Score must be >= 80%.
- No 5-point or 3-point requirements (except 3.13.11) can be POA&M’d.
- Only SOME 1-point requirements (including 3.13.11) can be POA&M’d.
- Five of the 1-point requirements cannot be POA&M’d.
- POA&Ms must be closed within 180 days.
CMMC Level 3:
- All requirements are worth 1 point.
- Assessment score must be >= 80%.
- 7 requirements cannot be POA&M’d.
- POA&MS must be closed within 180 days.
Furthermore, there cannot be any POA&Ms for external cloud services used that are not on the FedRAMP Marketplace, which need to be FedRAMP “equivalent.”
You can look up official guidance from the DoD.
In Closing
POA&Ms can appear like a complicated or cumbersome process; however, they are essential to tracking vulnerabilities and aiding in tracking the overall security posture of the system environment. In other words, it supports risk management, compliance, transparency, accountability, and continuous improvement in cybersecurity practices.
As your advisor during initial assessment or on an ongoing basis as part of a comprehensive continuous monitoring program, reach out to 38North Security, as we are happy to help make this a smooth process for your system environment.


