Cloud technology is a game-changer for both the government and private businesses. But with this reliance comes a pressing need for supply chain security to keep vulnerabilities and bad actors at bay. One method gaining traction is developing what’s called a Software Bill of Materials (SBOM) – a handy checklist to keep things in line.
Back in 2022 and 2023, the Executive Office of the President, Office of Management and Budget (OMB) issued M22-18 and M-23-16. These memos were all about tightening the screws on supply chain security and giving the software bill of materials a starring role in safeguarding government resources. The directive was clear: Federal agencies must keep tabs on the security of all their system components, including third-party cloud services.
When the government uses cloud services, those cloud services must be super secure, ticking all the compliance boxes like FedRAMP. That means the cloud service provider also needs to be on point with those requirements. And this is where the software bill of materials (SBOM) swoops in as the hero for both the Cloud Service Provider (CSP) and the agency using their Cloud Service Offering (CSO).
Learn more: FedRAMP’s Real Security Value Is in The Sound Baseline It Provides
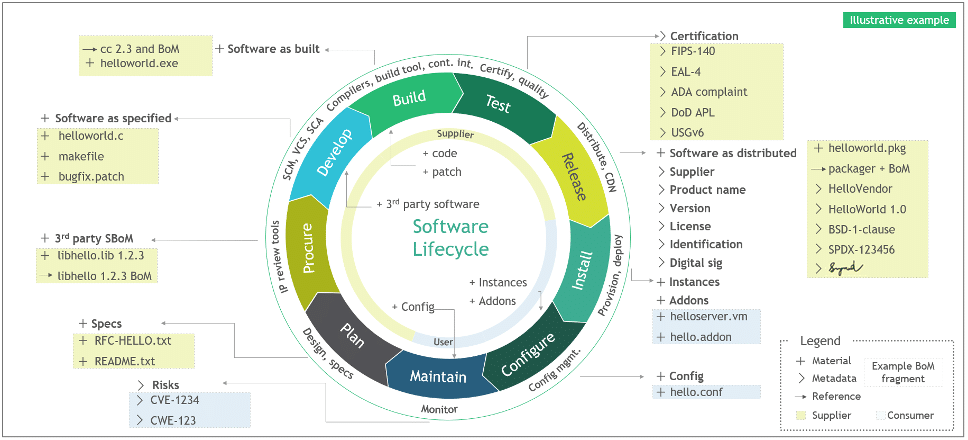
Why’s the SBOM such a big deal?
- Vulnerability Management: Think of the SBOM as the ultimate list of ingredients in the CSO cake. It helps both the CSP and the government keep an eagle eye on vulnerabilities, patch things up, and swiftly dodge risks.
When you have a detailed list of components to go down, tackling security issues becomes much more efficient and effective.
- Risk Assessment: The SBOM turns CSPs into security detectives, able to check the risks of their own software and dependencies.
For example, having an SBOM makes it easier for an internal compliance team to perform risk assessment.
Building this process into the overall development lifecycle also helps to identify potential security hiccups. It becomes easier to make informed decisions while building the software, keeping providers from introducing code from questionable sources that could cause trouble for the agency using their product.
- Incident Response: With cyber threats on the rise, being quick to react is crucial. The SBOM plays a critical role here, giving both the CSP and the agency the lowdown on what’s tangled up in the incident. That means they can figure out where things went south, fix it up, and prevent future attacks.
In other words, when there’s a fire, you’re not scrambling to figure out where the smoke is coming from.

In a world where cyber threats are getting craftier, having a solid supply chain with an SBOM is non-negotiable. It’s the map to spot and fix vulnerabilities, do risk checks before adding new stuff, and swiftly handle security incidents. Think of it as the VIP in a secure cloud System Development Lifecycle and overall supply chain management plan.
Contact us today to book a conversation with one of our experts to see how 38North can help you achieve your business goals.
Featured image: Runn Software


